31 | Add to Reading ListSource URL: planc.bizLanguage: English - Date: 2011-01-27 05:18:57
|
|---|
32 | Add to Reading ListSource URL: paiement.systempay.frLanguage: English - Date: 2015-12-16 04:48:58
|
|---|
33 | Add to Reading ListSource URL: www.conlog.co.zaLanguage: English - Date: 2015-11-26 07:18:35
|
|---|
34 | Add to Reading ListSource URL: www.emeraldgrouppublishing.comLanguage: English - Date: 2015-11-25 03:54:07
|
|---|
35 | Add to Reading ListSource URL: www.hkfoundersc.comLanguage: English - Date: 2015-06-22 02:44:30
|
|---|
36 | Add to Reading ListSource URL: norbert-pohlmann.comLanguage: English - Date: 2015-11-20 14:35:18
|
|---|
37 | Add to Reading ListSource URL: www.winlab.rutgers.eduLanguage: English - Date: 2013-04-18 23:09:49
|
|---|
38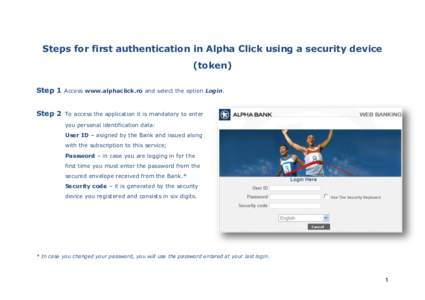 | Add to Reading ListSource URL: www.alphaclick.ro- Date: 2014-03-26 08:36:50
|
|---|
39 | Add to Reading ListSource URL: www.toshiba.co.jpLanguage: English - Date: 2013-07-31 22:51:17
|
|---|
40 | Add to Reading ListSource URL: www.entrustdatacard.comLanguage: English - Date: 2016-02-11 14:34:23
|
|---|